Infographic vector created by upklyak - www.freepik.com
Often times when I participate in Capture-the-Flag (CTF) events or engage in a penetration test, I'll need to send files from one computer to another. Sometimes I might transfer from Windows to Windows, Linux to Linux, or Windows to Linux and vice versa. In many cases, I need to transfer files to and from my Windows desktop (my host) to my Linux Virtual Machine (VM). During CTFs or penetration testing, it's imperative to know a variety of methods for transferring files between different machines and operating systems.
Sometimes during a CTF or a pentesting engagement, you'll need to grab files from a victim machine back to your attacking machine. Or, you might need to send your files from your Kali Linux VM (or other flavor of Linux) to your Windows machine for more permanent storage. In this blog, I'll show several different methods for transferring files.
Transferring Files
Many people in the cybersecurity/information security world rely heavily on VMware. VMware Tools allows users to seamlessly transfer files between their host operating system and their virtual machines. But, VMware licenses can be expensive and not everyone uses it.
I use ProxMox as my virtualization solution and haven't used VMware for a few years. Unfortunately, there isn't a VMware Tools equivalent for copying/pasting or transferring files from your host to your ProxMox VMs. I've found a few creative solutions that have worked for me.
Copying and Pasting with Netcat (Windows to Linux)
Using this method requires downloading Netcat for Windows (if you're using Windows). Download and install netcat, then follow the steps below.
Let's say I have the following machines and IPs that I want to copy/paste between:
- Windows (192.168.1.10)
- Linux (192.168.1.20)
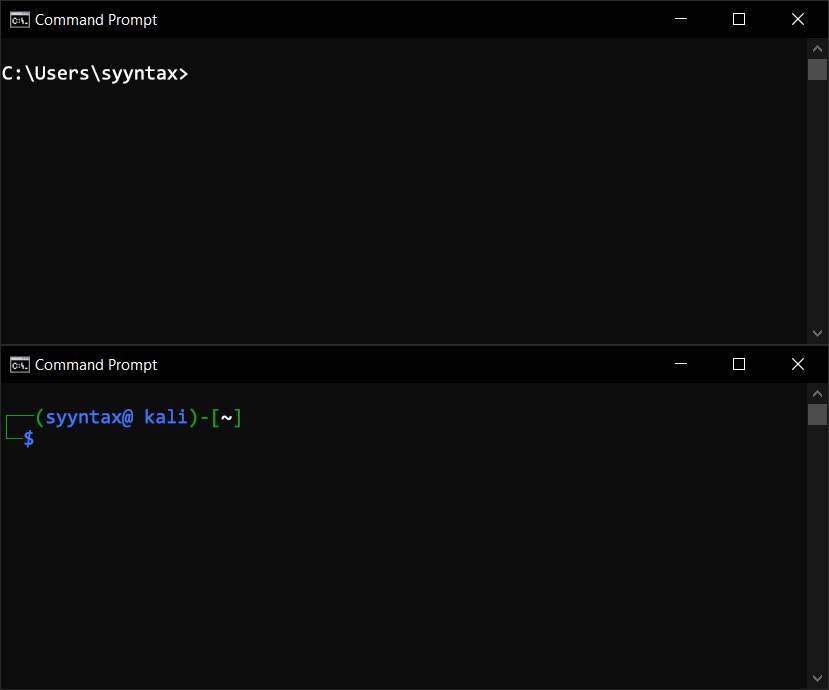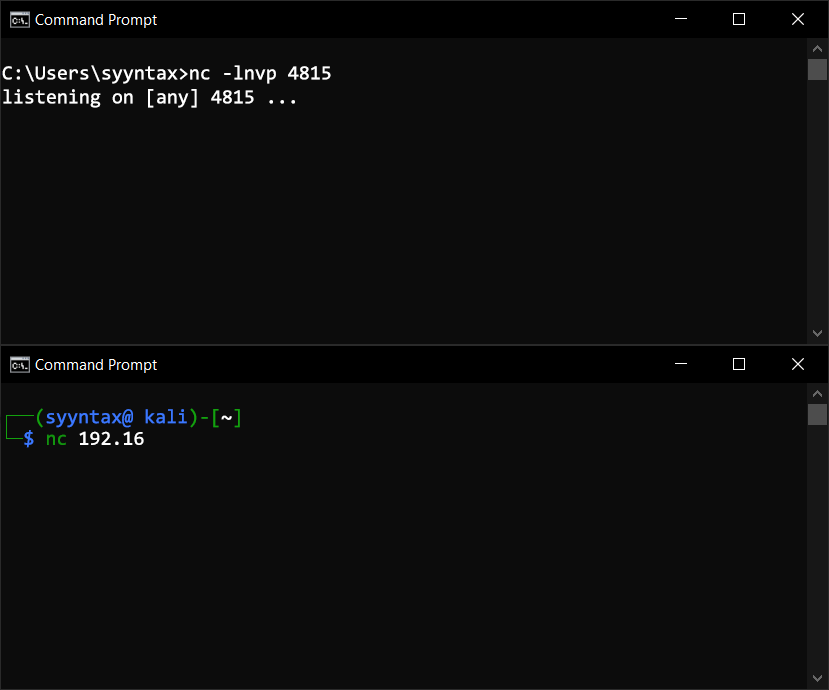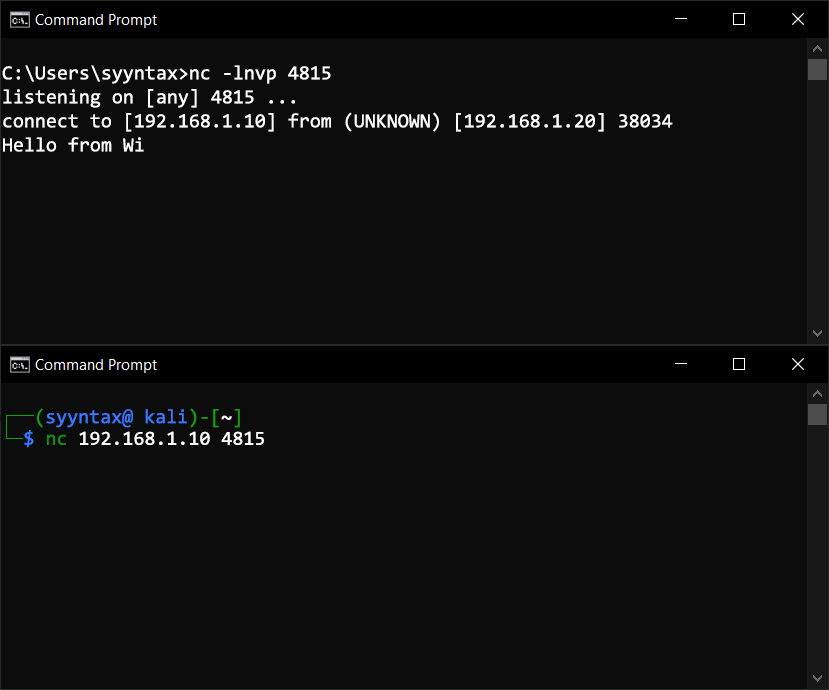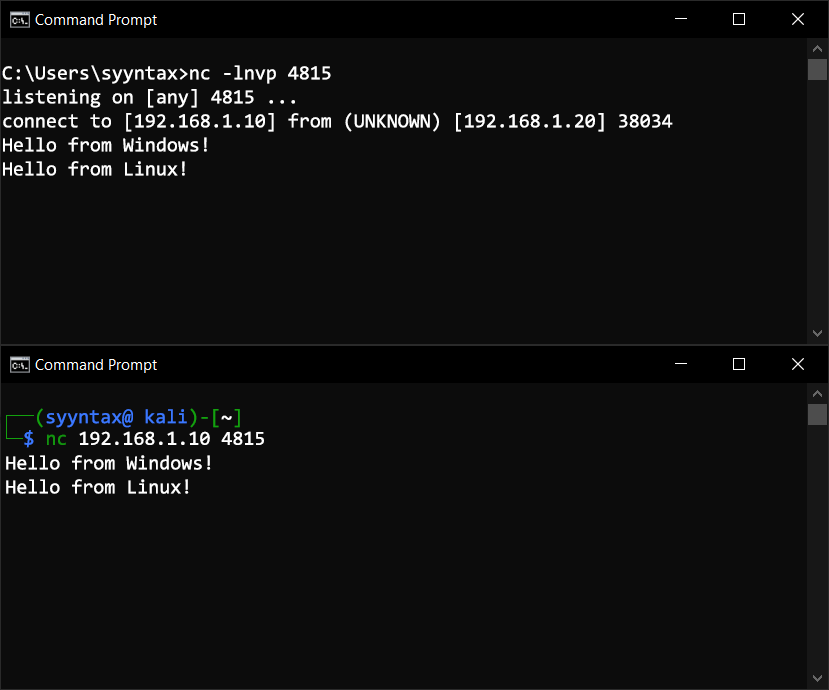
First, open a Command Prompt (Hold Win+R, then type "cmd"). Enter the following command to start a Netcat listener on a port (I used port 4815 in my example).
C:\> nc -lnvp 4815Now, from your Linux VM, connect to the listener using the following command:
$ nc 192.168.1.10 4815If you enter text in one terminal and press Enter, you'll see the text appear in the other machine's terminal. You can also copy text and paste it rather than typing it in.
Sending files with Netcat
Sending files with Netcat is very easy. The only downside to this method is that Netcat is not native to Windows.
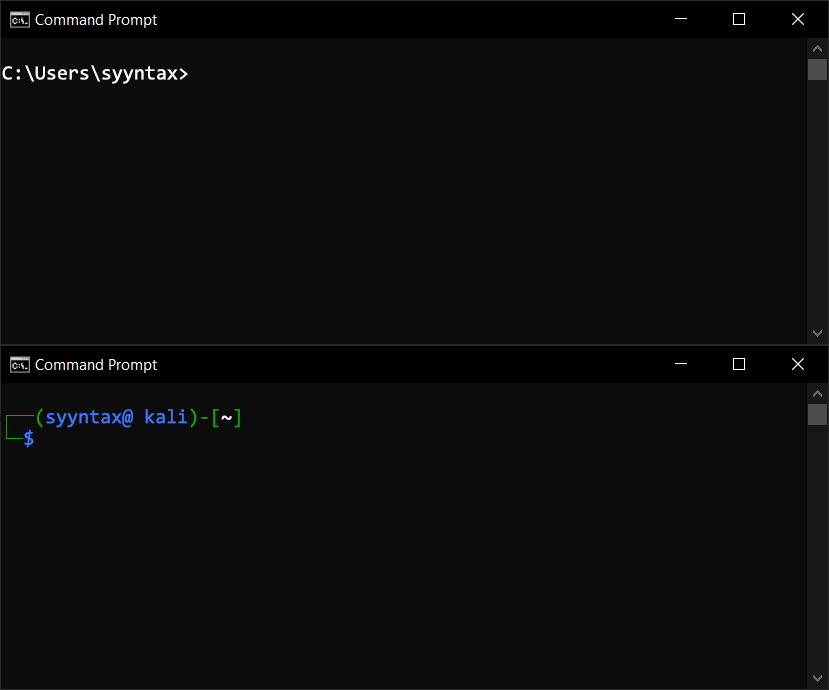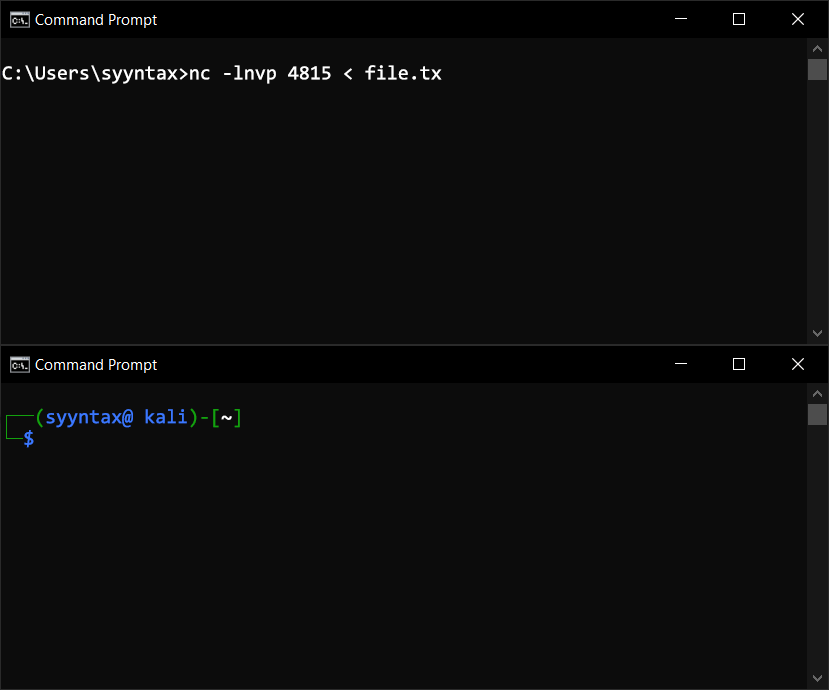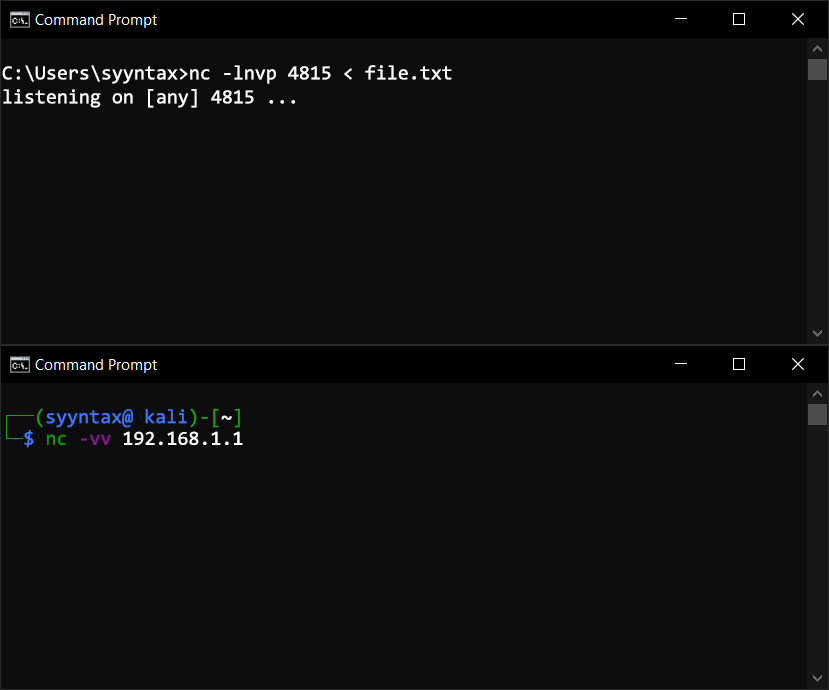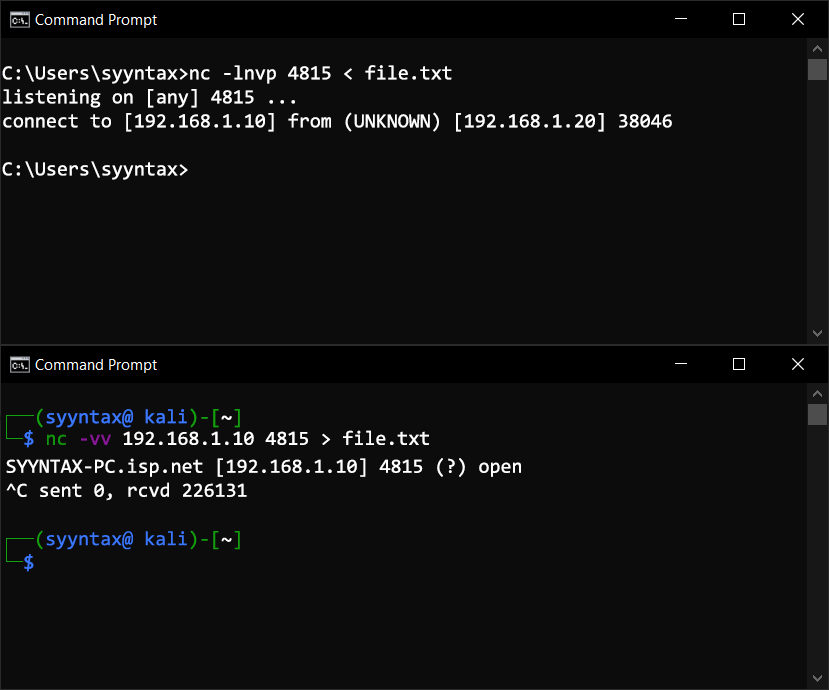
Send the file through the Netcat listener:
C:\> nc -lnvp 4815 < path\to\file.txtReceive the file on your Linux VM:
$ nc 192.168.1.10 4815 > file.txtThis works if you reverse the process as well and send from Linux and receive on Windows.
Sending Files with Python
You can also use Python's HTTP server to send files. For this method, only the sender needs to have Python installed. There are a ton of ways you can send files using Python; I'm only going to touch on the HTTP server method.
First, navigate to the directory (folder) that you want to expose to the receiving client. Then, start the HTTP server:
$ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...If you're a caveman and still using the deprecated Python 2.7, use HTTPServer instead of http.server.
On the Windows host, open a browser and navigate to the sender's IP address on port 8000: http://192.168.1.20:8000. You'll see a list of contents; download the file you want to receive.
Sending Files with Secure Copy (SCP)
Assuming both systems have Secure Shell (SSH) installed, you can use SCP to copy a file from one machine to another. This is possible on Windows if you have installed and enabled the Linux subsystem for Windows.
As is the case with the previous methods, open a Command Prompt or terminal and run scp. The command syntax looks like this when using a password:
scp <source file> <user>@<IP or domain>:<path/to/file>
Push a file to a remote host using this command:
C:\Users\syyntax>scp file.txt syyntax@192.168.1.20:/home/syyntax/DocumentsPull a file from a remote host using this command:
C:\Users\syyntax>scp syyntax@192.168.1.20:/home/syyntax/Documents/file.txt file.txtSending Images between Windows and Linux
Now, let's say you're in a situation where you need to send a file from Windows to Linux, but the Windows machine doesn't have netcat, scp, or python installed. This commonly happens in pentesting engagements when you successfully break into a Windows machine and need to pull files (without an easy method like meterpreter). This may not be the most efficient method, but it works.
Use Certutil to get Hex Values
From the Windows machine, use the certutil tool to grab the hexadecimal values of the file. In my example, I want to pull sensitive.pdf from my victim's machine, but all I have is a shell and no means of transferring the file. I use certutil to output the file's hexadecimal values to sensitive.txt. Then, I use type to see the data.
C:\Users\victim>certutil -encodehex -UnicodeText sensitive.pdf sensitive.txt
Input Length = 48442
Output Length = 224066
CertUtil: -encodehex command completed successfully.Read the Hex File Contents
Read the data with type:
C:\Users\victim>type sensitive.txt
0000 25 50 44 46 2d 31 2e 36 0d 25 e2 e3 cf d3 0d 0a %PDF-1.6.%......
0010 31 30 20 30 20 6f 62 6a 0d 3c 3c 2f 4c 69 6e 65 10 0 obj.<</Line
0020 61 72 69 7a 65 64 20 31 2f 4c 20 34 38 34 34 32 arized 1/L 48442
0030 2f 4f 20 31 32 2f 45 20 34 34 31 32 35 2f 4e 20 /O 12/E 44125/N
0040 31 2f 54 20 34 38 31 34 30 2f 48 20 5b 20 35 31 1/T 48140/H [ 51
0050 36 20 31 39 34 5d 3e 3e 0d 65 6e 64 6f 62 6a 0d 6 194]>>.endobj.
0060 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20 20
0070 20 20 0d 0a 33 37 20 30 20 6f 62 6a 0d 3c 3c 2f ..37 0 obj.<</
...The output might be very long, so you may need to increase your terminal's buffer size if possible. From here, I'll highlight the contents of sensitive.txt and copy.
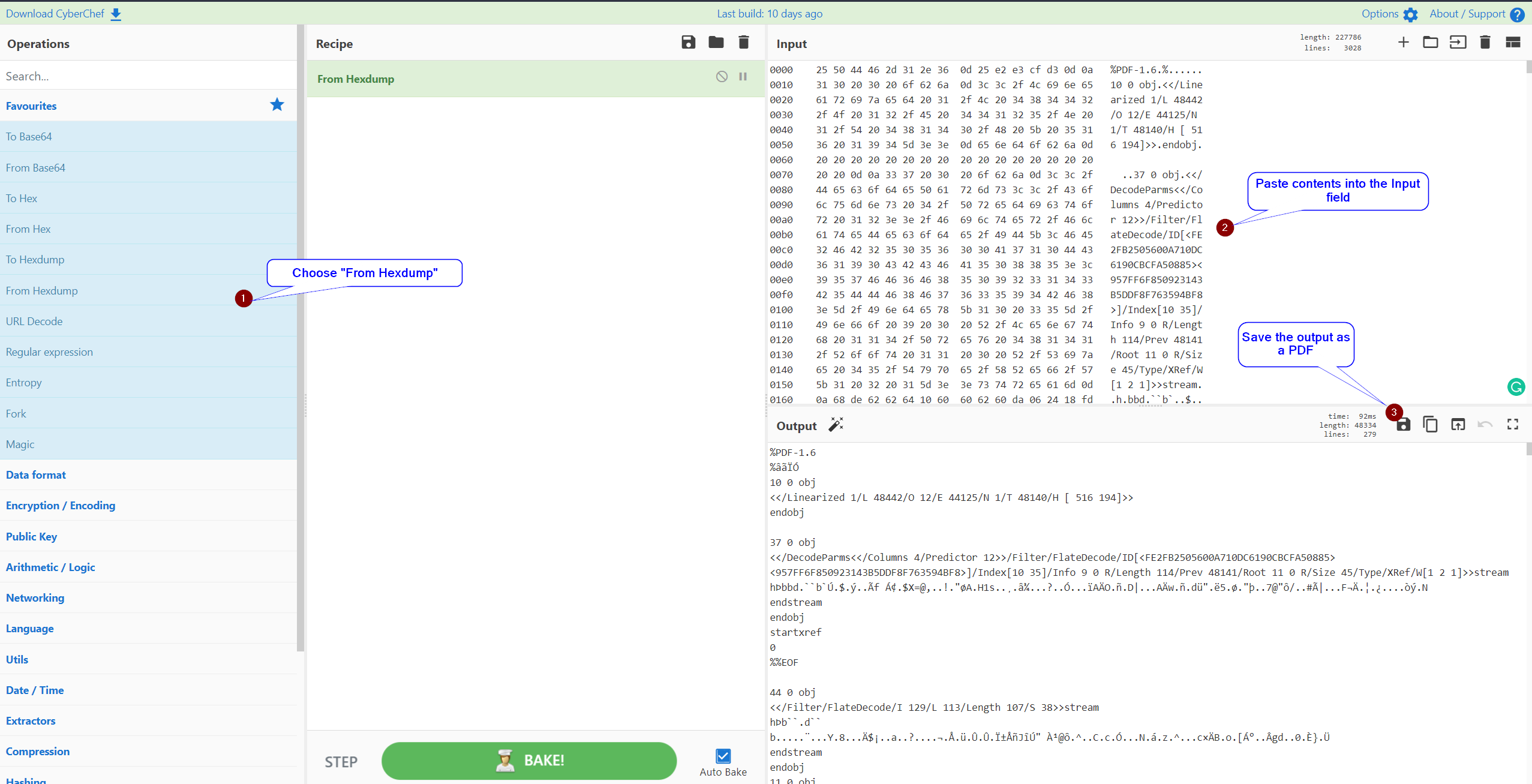
Plug the Content into Cyber Chef
If you've read many of my blogs here, you know I'm a big fan of Cyber Chef. Navigate to https://gchq.github.io/CyberChef/ and use the From Hexdump recipe. Paste the contents of the sensitive.txt file into the Input field on the right-hand pane.
In the Output field, click on the Save icon and save the file to your machine as a PDF (for example, I saved it as sensitive-doc.pdf.
Open the PDF and you'll see the contents of the file.
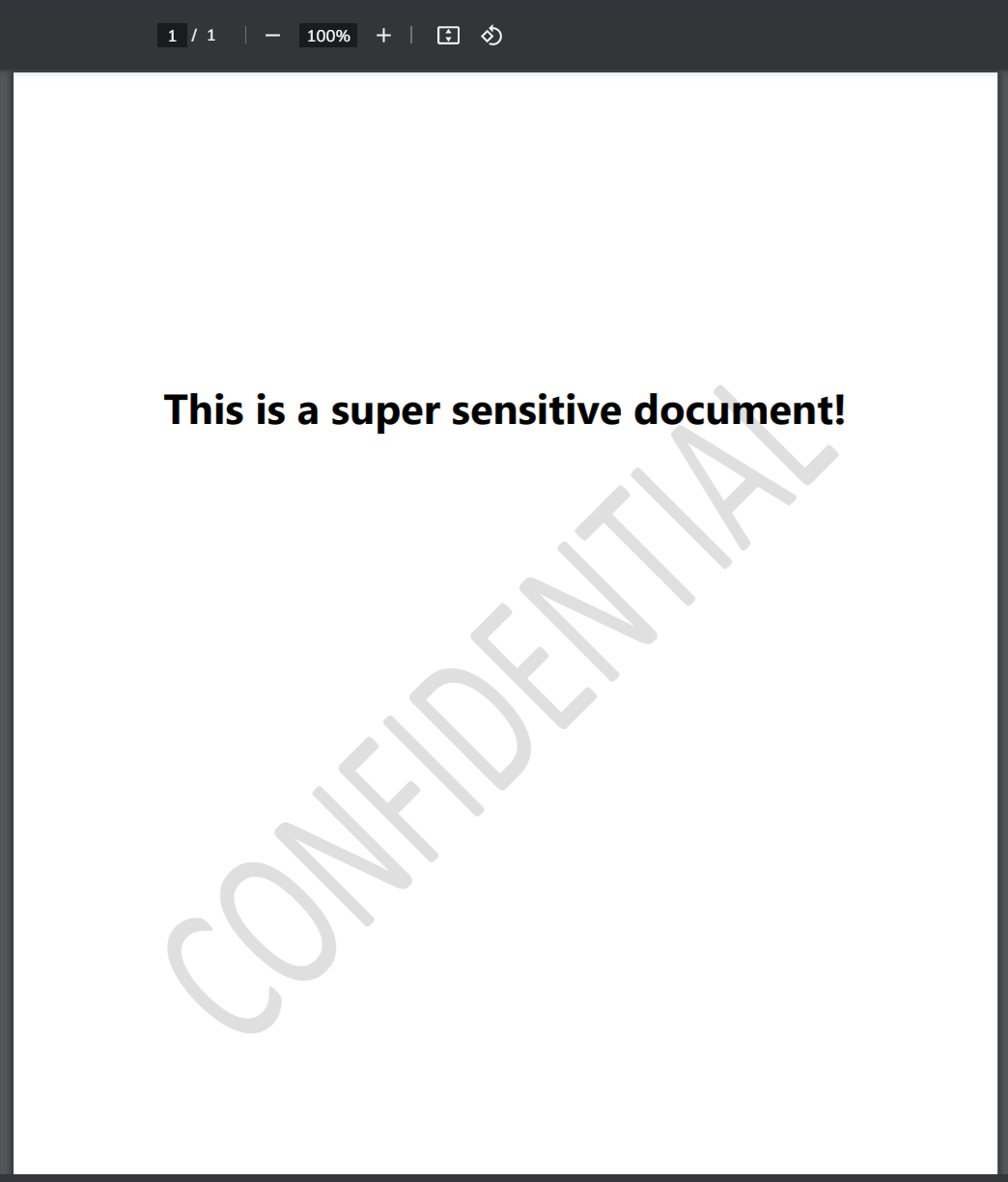
You can use this method with almost any file!
Conclusion
These are just a few examples of the many ways in which you can transfer files or copy and paste text from either two remote operating systems or between your host and a VM. If you have any other methods that you use, let us know at info@cyberhacktics.com!