In my previous blog, I demonstrated how winpmem can be used to capture memory from a computer, and how Volatility can be used to analyze that memory. I briefly walked through the steps for analyzing processes and determining obvious signs of malicious processes. I also went over how to sort through network connections in a memory dump.
In this blog, I'll be continuing from where I left off in my previous blog. I'll demonstrate how to carve out the malicious explorer.exe executable that was found in the memory dump file. I'll also show how to extract password hashes and crack the password.
Extract the Malicious Executable
If you suspect that a process is malicious, you can extract it from the memory dump using the procdump plugin in Volatility. I used the following command to carve out the process:
volatility -f memdump.raw --profile=Win10x64_10586 procdump -D ./ -p 4620In my command, I used the -D (or, --dump-dir) option to designate where I wanted to save the extracted process. The ./ argument tells Volatility to save the extracted process in the present working directory. The -p 4620 option tells Volatility to extract the process with a PID of 4620.
Volatility Foundation Volatility Framework 2.6
Process(V) ImageBase Name Result
------------------ ------------------ -------------------- ------
0xffffbd8528ec9080 0x0000000000400000 explorer.exe OK: executable.4620.exeThe output shows that the process was successfully extracted and saved as exectutable.4620.exe.
A Quick Disclaimer
It's important to note that when you extract known or potential malware from a memory dump, you run the risk of infecting your machine if the executable is ran. Always perform malware analysis in a sandboxed environment like a virtual machine that is isolated from other systems on your network.
Look It Up
Once you have the extracted executable, one of the first steps should be to use a tool like VirusTotal to see if you can find information from the larger community about the file. In my analysis, I first obtained the MD5 hash of the file using the md5sum tool in Kali Linux.
md5sum executable.4620.exeb81efd31b84e6434828eba274ac9626b executable.4620.exeI copied the MD5 hash (i.e. b81efd31b84e6434828eba274ac9626b) and searched for it in VirusTotal.
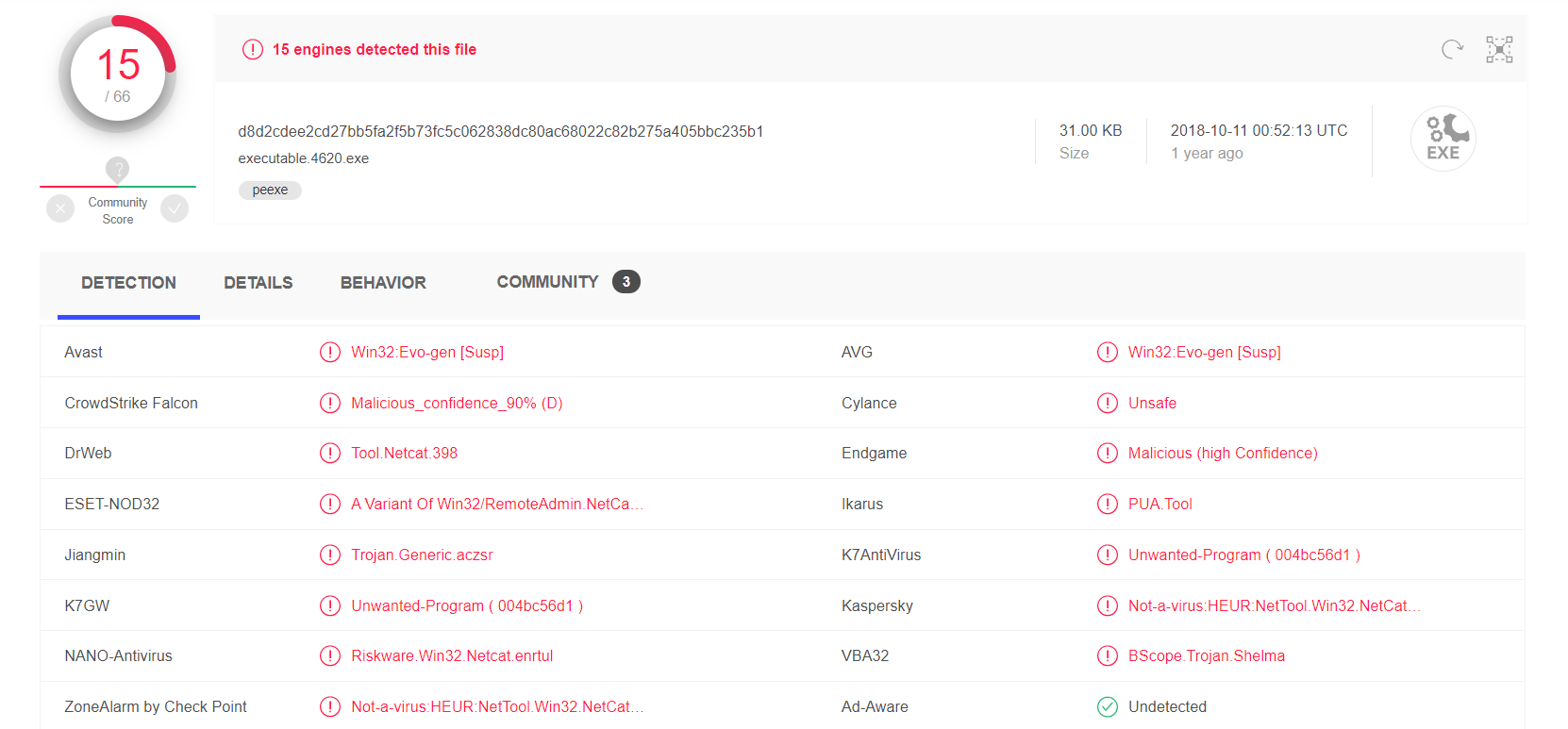
Looking at the results, it can be determined that this file is NetCat. While NetCat is not necessarily malicious and does have legitimate practical usage, it's functionality can lend to malicious attacks. It is uncommon to see NetCat in most Windows environments.
Obtaining Passwords
Memory dumps can also contain password hashes on a system. These hashes are not the passwords themselves, but if users have common passwords that can be found in password lists, then it is easy to perform a dictionary attack on the hashes to determine the password.
To obtain the passwords, I used the hashdump plugin in Volatility.
volatility -f dump --profile=Win10x64_10586 hashdumpVolatility Foundation Volatility Framework 2.6
Administrator:500:53955181458a4cb24126d9124127f42f:82811a2eb49a6d3c51aa8175b7efb8c8:::
Harold:501:6089b6316b3577c480e849a27cb2f122:3e24dcead23468ce597d6883c576f657:::
DefaultAccount:503:5c6399d3e379ade9ed52e19f038cc6b4:690af36e2dcf6fff7b723ccd2a820151:::Volatility dumped these three passwords. The Harold account is the normal user's account. I copied this hash into a text file I named hashdump.txt and used a password cracking tool called John the Ripper to discover the password.
john --format=NT hashdump.txt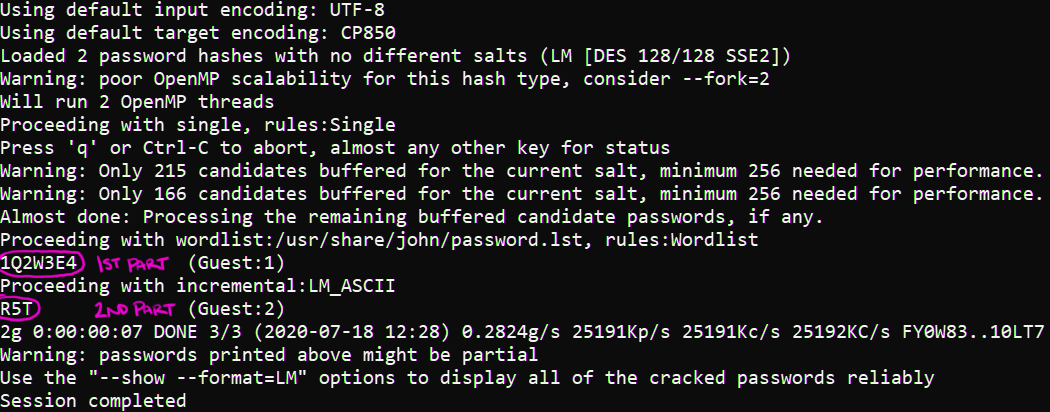
Looking at the output above, we can see that the password for Harold is 1Q2W3E4R5T. This password was cracked within a matter of seconds. Don't let the combination of letters and numbers trick you into thinking this password is secure - it's not. In fact, this password was identified as one of the top 20 most used (and hacked) passwords of 2019.
Conclusion
Volatility is a powerful memory forensics tool. More than just providing a tool to analyze memory, it can also carve out files and dump sensitive information like password hashes. Carving out files helps analysts to research and investigate malware in a controlled environment. It might also help them determine what kind of information could have been compromised on an infected host.


