In network penetration testing, meticulous planning lays the groundwork for a successful and impactful campaign. This blog explores the pivotal role of planning, emphasizing its significance in ensuring a comprehensive and efficient penetration testing process. From defining the scope to identifying objectives, every step in the planning phase contributes to the effectiveness of the overall assessment.
Importance of Planning
Planning serves as the compass, guiding pentesters through the intricacies of network assessments. It involves a thorough understanding of the organization's structure, its assets, and potential vulnerabilities. By identifying the objectives and constraints early in the process, pentesters can tailor their approach to meet specific goals, ensuring a focused and targeted assessment.
Before any testing is accomplished, you should first make sure you know your scope and Rules of Engagement (ROEs). In my line of work, ROEs and other coordination are documented in the Statement of Work (SOW). Planning is usually the least exciting part of a pentest for most people; however, it is undoubtedly one of the most important phases. Failure to properly plan a pentest can result in criminal charges, fines, and a hit to your reputation as a credible and professional pentester.
Rules of Engagement
Rules of Engagement (ROEs) act as the cornerstone of a pentesting engagement, delineating the boundaries and expectations for both the client and the pentester. These documented guidelines are signed by all parties involved, fostering a clear understanding of the testing parameters. Addressing crucial aspects such as standards to be tested against, the type of tests, constraints, restraints, testing schedule, and the scope of the test, ROEs provide a structured framework that safeguards against potential pitfalls and ensures a mutually beneficial engagement.
Some common things addressed in ROEs include:
- Standards that will be tested against (e.g., PCI-DSS, HIPAA, and etc.)
- Type of tests being conducted (e.g., black box external, web application test, and etc.)
- Constraints (things that must be accomplished during the test)
- Restraints (things that must not happen during the test)
- Testing schedule (e.g., 24/7, business hours only, weekends only, and etc.)
- IPs or domains from which testing will originate (i.e., the "attacker's" IP)
- Scope of the test
Scope
Understanding the scope of a pentest is paramount as it delineates the boundaries within which the assessment will unfold. Clearly defining what IPs, domains, URLs, and applications are in scope ensures a targeted and purposeful testing approach. Equally crucial is the delineation of out-of-scope elements, preventing unintended consequences like testing against production systems that could lead to service disruptions or inadvertently exposing sensitive information. A well-defined scope not only aligns the expectations of both the client and the pentester but also minimizes the risk of collateral damage and enhances the precision and relevance of the pentest results.
Constraints
Constraints established during the planning phase are essential components that shape the dynamics of a pentest. These limitations, often specified by the client, ensure a controlled and compliant testing environment.
Clients will usually ask for certain requirements. Below are some examples of constraints:
- Communicate with client via email if a critical vulnerability is found
- Communicate with local law enforcement if suspected criminal activity is found
- Deliver a status report at the end of each testing window
Restraints
Restraints are the opposite of constraints. These are things that must not happen during a pentest. Below are some examples of restraints:
- Do not conduct active scans against https://test.example.com
- Do not exercise social engineering
Stay Organized
It's important to keep organized notes during a pentest. If a client asks you to describe what led you to a finding, it's helpful to have documentation that can be referenced. I use AnyType to document my pentests. I really enjoy their object-oriented note-taking approach, where notes are treated as objects that can relate to other notes. In AnyType, I keep a checklist of tasks I need to accomplish throughout the test. The image below is the template from where I start, although I usually add cards throughout the test as needed.
Build a Workspace
I normally use Kali Linux when I conduct my pentests. In Kali, I set up a folder structure for each client that looks similar to the one below:
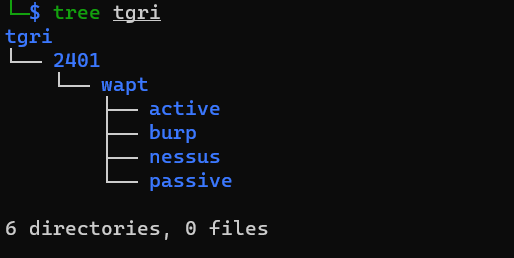
This is just the boilerplate template - I usually add folders and files as I proceed throughout the pentest. These folders are also where I store screenshots and output files.
To-Do Checklist
I keep a To-Do checklist to make sure that I accomplish everything needed in the pentest. Here are the checklist items I follow (this is not an all-inclusive list - I add to this checklist for every engagement):
- Ensure SOW and project questionnaire is signed by the client
- Send an introductory email to the client
- Create project folder
- Verify project scope
- Characterize the client's external presence
- Identify emails/users
- Identify breached passwords
- Attempt to enumerate accounts
- Run a vulnerability assessment scan
- Conduct manual testing/validation of identified vulnerabilities
- Conduct password spraying and brute force on login portals
- Escalate access from external to internal
- Cleanup
- Write the report
Not every checklist item will be hit, but this is a good roadmap to ensure I cover my bases when running the pentest engagement.
Communication
Finally, another important aspect of planning is knowing how, when, and what to communicate with the client. Communication constraints should be included in the ROEs; the important thing is to make sure that you communicate with the client when you find anything of critical importance.
Conclusion
Planning is one of the most important steps before you begin a pentest. It's in planning that you identify the client's requirements and the bounds that you need to stay within. Knowing and adhering to these will not only ensure a successful pentest but will also protect you from adverse consequences. And remember, having a plan for an organized, structured test will not only lead to a successful pentest but will also lend to your credibility and professionalism.
In the next blog, I will walk through my process for conducting passive reconnaissance.


